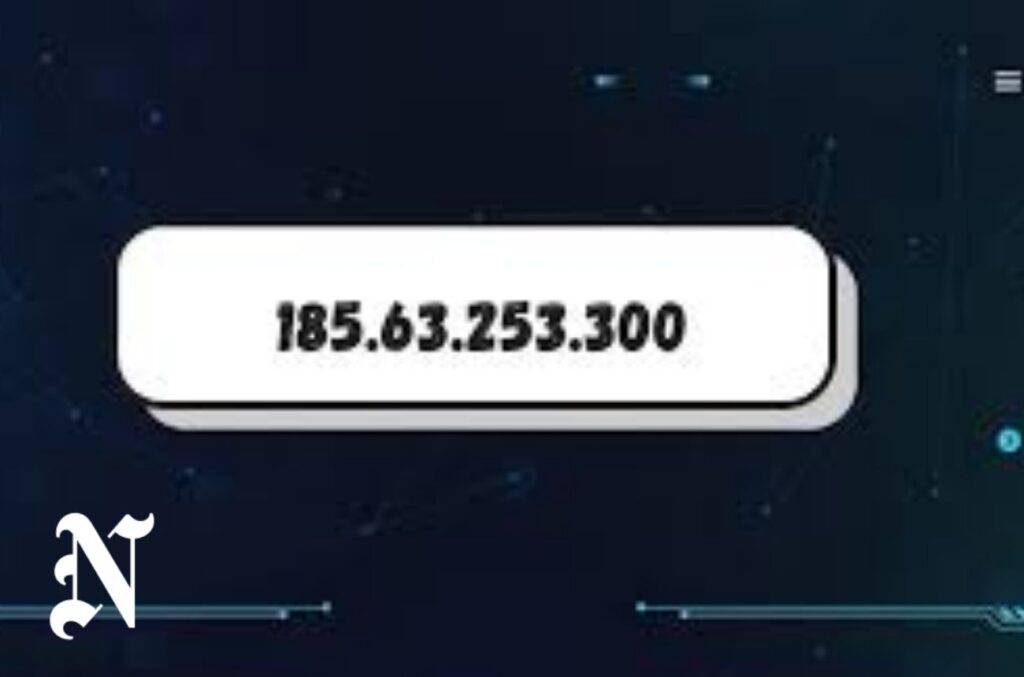
In the ever-evolving world of digital networks and cybersecurity, IP addresses serve as crucial identifiers for devices online. A frequently cited example, 185.63.253.300, has generated interest among developers, analysts, and cybersecurity enthusiasts alike. While this address may appear standard at first glance, its structure reveals a technical inaccuracy that highlights deeper insights into how internet protocols work.
In this article, we’ll explore everything from IP address fundamentals to advanced threat intelligence applications — all centered around the IP format 185.63.253.300. Although it is technically invalid, this address is often used in education, cybersecurity training, and DNS testing. This guide will help you understand its relevance, implications, and how IP addresses shape our digital interactions.
What Is 185.63.253.300?
The IP address 185.63.253.300 resembles a standard IPv4 address format: four numbers separated by periods. Each segment (known as an octet) must be a value from 0 to 255. The presence of “300” in the final octet renders this address invalid in technical terms.
So why is it used?
Often, such addresses serve demonstrative or placeholder purposes in documentation, test environments, and cybersecurity simulations. While 185.63.253.300 doesn’t function in real-world networking, it provides a useful case study in understanding IP structure errors and validation mechanisms.
Understanding IP Address Structure
An IPv4 address consists of 32 bits, divided into four 8-bit sections. Each 8-bit section (octet) can represent values from 0 to 255, meaning any octet exceeding 255 breaks IPv4 rules.
Here’s what that looks like:
-
Valid IPv4:
185.63.253.200 -
Invalid IPv4:
185.63.253.300(300 > 255)
In binary:
-
Maximum valid octet:
11111111(Decimal: 255) -
Invalid: 300 exceeds the 8-bit capacity and cannot be represented in standard IPv4.
This helps systems instantly identify and reject such invalid IPs, improving data integrity and routing accuracy.
Why 185.63.253.300 Appears in DNS Checkers
Despite its invalidity, 185.63.253.300 often shows up in DNS checker tools, test logs, and simulation software. Why?
-
DNS Testing: Developers use placeholder IPs to test DNS propagation without risking real server connections.
-
Network Training: Used in labs to teach students how to detect and correct IP errors.
-
Threat Simulation: Cybersecurity teams may simulate attacks from spoofed IPs like 185.63.253.300 to test firewall rules and intrusion detection systems (IDS).
These uses reinforce the value of understanding both valid and invalid IP structures.
Cybersecurity Implications of Invalid IPs
Cybercriminals often manipulate IP addresses in logs, making it appear as though traffic originates from an address like 185.63.253.300. These spoofed IPs confuse automated monitoring systems or help hide the attacker’s true origin.
In practice:
-
Intrusion Detection Systems (IDS) flag such anomalies.
-
Firewalls block invalid requests.
-
Security analysts use these markers to investigate spoofing attempts.
Thus, 185.63.253.300 becomes more than a formatting error — it’s a potential signal in threat intelligence systems.
DNS Resolution and 185.63.253.300
The Domain Name System (DNS) translates human-friendly domain names into machine-friendly IP addresses. When DNS systems encounter 185.63.253.300, they:
-
Return an error or NULL response due to invalid format.
-
May log the request for forensic analysis.
Such cases help DNS administrators identify malformed queries, possible misconfigurations, or malicious probing attempts on their servers.
Real-World Examples and Use Cases

Though 185.63.253.300 is not assigned to any live host, here are real-world uses:
| Scenario | Role of 185.63.253.300 |
|---|---|
| Cybersecurity Training | Used to simulate spoofed traffic |
| DNS Debugging | Tested for handling invalid entries |
| Network Tools | Placeholder in IP scanning tools |
| Log Analysis | Flagged as anomalous input |
| Coding Examples | Used in technical documentation |
These roles make it a key player in network education and simulation.
Comparison: IPv4 vs IPv6
The IP format of 185.63.253.300 highlights a core limitation of IPv4 — the finite address space. As we move into a more connected world, IPv6 solves this problem.
| Feature | IPv4 | IPv6 |
|---|---|---|
| Address Length | 32 bits | 128 bits |
| Format | 4 octets | 8 groups |
| Capacity | 4.3 billion addresses | 340 undecillion |
| Example | 185.63.253.200 | 2001:0db8:85a3::8a2e:0370:7334 |
IPv6 virtually eliminates the need for placeholder addresses like 185.63.253.300.
IP Address Validation in Software
Web applications and firewalls validate IP inputs to prevent errors and misuse. When a user or process submits 185.63.253.300:
-
Input validation fails: The number 300 is out of range.
-
API or script rejects the IP entry.
-
Logs may note it as a potential malicious input.
This makes validation essential in user forms, config files, and system utilities.
How Mistyped IPs Cause Downtime
Imagine configuring a server with 185.63.253.300 as a DNS forwarder. The result?
-
Service failure due to unreachable address.
-
No DNS resolution, leading to errors across services.
-
Increased support tickets as users can’t access resources.
Network teams often discover these issues during routine audits or when tracing connectivity failures.
Education and Awareness

IP addresses like 185.63.253.300 serve as teaching tools. They help newcomers and professionals:
-
Understand address limits.
-
Explore IP spoofing.
-
Learn DNS mechanics.
-
Practice log investigation.
-
Apply firewall filtering rules.
This theoretical IP is commonly featured in certification prep, such as CompTIA, CEH, or CCNA.
How to Spot Invalid IPs in Logs
During log reviews, invalid IPs like 185.63.253.300 are red flags. You might see:
-
Denied connections with unusual last octet.
-
Unusual spikes in traffic from such IPs.
-
Patterns showing automation scripts or scanning tools.
Security teams tag these logs and use them for incident analysis and threat intelligence feeds.
The Future of Addressing
IPv6 adoption is slowly but steadily increasing, and systems are being built to deprecate reliance on IPv4 structures.
Still, until full transition:
-
Invalid IPv4s like 185.63.253.300 will continue to be used in test scenarios.
-
Education systems will reference them for training exercises.
-
Tools will evolve to catch and handle them more efficiently.
Final Thoughts
Although 185.63.253.300 isn’t valid in any functional network, its presence in tools, simulations, and logs makes it invaluable for education, threat modeling, and DNS analysis.
It teaches:
-
IP structure integrity
-
Threat detection methodologies
-
The importance of validation
-
Safe DNS configurations
-
The transition toward IPv6
Understanding such addresses isn’t just about rules — it’s about building safer, smarter digital infrastructure.